Blogs
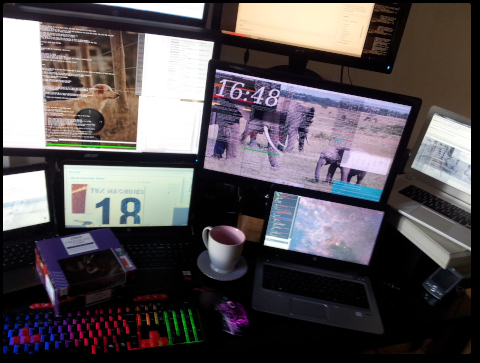
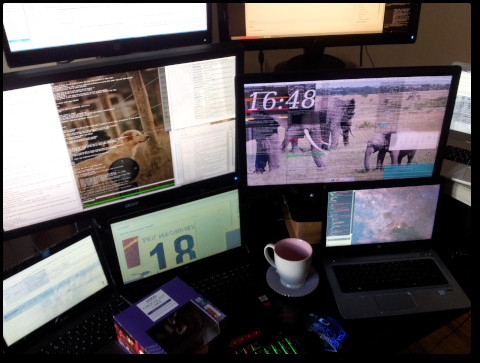
Photos: Tux Machines at 18
Submitted by Roy Schestowitz on Friday 10th of June 2022 06:36:17 PM Filed under
We're Eighteen Today
Submitted by Roy Schestowitz on Thursday 9th of June 2022 11:04:26 PM Filed under
TODAY is a special day because tuxmachines.org was registered exactly 18 years ago. We recently renewed this domain's registration for 5 more years (i.e. until middle of 2027) as we certainly expect the site to go on and on for a long time to come.
As people who do technology for a living, with a focus on Free software in particular, running this site is also an educational experience. It helps keep track of what's happening (e.g. new releases, security patches) and if other people find our news picks useful, it motivates us to keep it updated 24/7 every day of the year. We of course receive a lot of help from submitters who themselves produce original works (articles). A personal word of gratitude to all and an outlook (as video):
Video download link | md5sum 7db0f40f2834a02615c5a7d16a7151b2
Turning 18
Creative Commons Attribution-No Derivative Works 4.0
tuxmachines.org is a very busy news hub. Before Alexa.com was shut down (and we before we shunned Phoronix) Alexa said that tuxmachines.org was the biggest source of traffic to Phoronix. █

- Roy Schestowitz's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- 13620 reads
 PDF version
PDF version
Tux Machines All Grown Up Soon
Submitted by Roy Schestowitz on Monday 30th of May 2022 07:24:11 AM Filed under

Coming soon!
IN a matter of days we'll celebrate our birthday or anniversary. It started in 2004 and it's still going strong.
We have some potential improvements for the site in mind.
- Roy Schestowitz's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- 12257 reads
 PDF version
PDF version
We Turn 18 Next Month
Submitted by Roy Schestowitz on Wednesday 11th of May 2022 12:42:47 AM Filed under

A month from now this site turns 18. No special event is planned, but we're gratified to have come this far. Days ago we registered the domain for 5 more years (2027), seeing that everything continues to grow, just like GNU/Linux itself (along with BSDs). Thanks to the many people who choose this site as their daily "news fix"...
We remain apprehensive about social control media, including Twitter. We suggest people subscribe via RSS rather than external third parties. The latter simply cannot be relied on. For instance, earlier this year JoinDiaspora joined the many dead Diaspora pods; it shut down and we had to start a new account in another pod, taking us down from thousands of subscribers to only zero. █
- Roy Schestowitz's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- 13667 reads
 PDF version
PDF version
Migration of Diaspora Account
Submitted by Roy Schestowitz on Thursday 10th of March 2022 05:08:42 AM Filed under

If you have been following Tux Machines over Diaspora, be sure to update to the existing pod, psyco.fr. Our account is here following the shutdown of the JoinDiaspora pod earlier this month.
- Roy Schestowitz's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- 14908 reads
 PDF version
PDF version
Be Careful What You Wish For...
Submitted by Roy Schestowitz on Thursday 3rd of March 2022 09:55:38 PM Filed under

A CONCEPT like "Free software" was formulated more than 38 years ago at MIT (United States). Linux, the kernel, came from a neighbour of Russia in 1991. The father of Linus Torvalds is a politician known for his connections to Russia; he encouraged non-confrontational politics, the mindset of co-existence. At the moment there are attempts to leverage Free software projects for political purposes, mostly by banning Russians and sometimes Belarusians (collective punishment). This approach is deeply misguided because it's unlikely to accomplish anything except harm to Free software. It's striking at the very core of what GNU/Linux is and what it stands for. Be careful what you wish for... █
- Roy Schestowitz's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 15518 reads
 PDF version
PDF version
Microsoft is Faking It and Windows Market Share Worldwide Now Lowest Since the Release of Vista 11
Submitted by Roy Schestowitz on Wednesday 2nd of March 2022 10:54:08 PM Filed under
With February now over, let's examine the actual numbers; Microsoft boasts "success", but that's just "fake news"...


- Roy Schestowitz's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- 16502 reads
 PDF version
PDF version
Our 18-Year Anniversary is Fast Approaching and We Move on From JoinDiaspora
Submitted by Roy Schestowitz on Monday 28th of February 2022 01:02:07 AM Filed under
Almost 2,500 "followers" will be lost
OVER the past couple of years we've not done anything special in site anniversaries, except the 15th (months before the COVID-19 outbreak). We'll soon change our account in Diaspora because JoinDiaspora is shutting down. Our account had been there for over a decade, even before it was adopted by TuxMachines, but all things come to an end. We'll say more nearer to the time of migration (some time in March). █
- Roy Schestowitz's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- 16471 reads
 PDF version
PDF version
The Command Line Challenge
Submitted by Roy Schestowitz on Monday 17th of January 2022 10:10:50 PM Filed under
Authored by Andy Farnell

Cheapskates wonderful guide is currently running a "One Week Command Line Challenge". Some of the students I teach now are so young (to an old beard like me) they think this is some "crazy new thing". Is there new hope and a new perspective to be explored here? Something other than retro and cool. Perhaps historical baggage, the narrative of how "superior" graphical interfaces replaced "old" consoles is an obstacle to new visions for the next generation?
As a lifelong textual user interface (TUI) user this got me thinking. If you were to give me "The GUI Challenge" I'd be sunk! My world (dwm, emacs, w3m etc) feels so familiar, it's in my bones. After thirty or forty years on the command line if I were forced to use "normal computers" it would cripple my ability to do anything.
The command-line is super empowering, but particular. Put me on a Mac or Windows machine and I revert to a child-like flap, randomly clicking around on icons that look promising. I'd be twenty times less productive than my peers, yet, modesty be damned, I'm ten times more effective/productive at average computing tasks than other professionals when in my comfort zone - at the command-line. Isn't this true for us all, that we have our comfy shoes?
Of course this isn't about some innate inability to use graphical tools. I've mastered some jolly complex ones like Blender and Unreal editors (virtual world building), and ProTools or Ardour (for sound and music). One of the most complex I recall was a VLSI/CAD creator that used two four button mice (or mouse and ball).
So, is the command line challenge unfair? I am no more capable of quickly learning a new graphical paradigm than an entrenched GUI user is of adopting the keyboard and console. This probably applies at any age or ability level where you are comparing like-for-like paradigm switching.
No, the issue here is deeper and is about utility paradigms. How do people relate to computers as tools at the highest level - at the operating system level and above?
If you dig back in the Usenet and mailing-list archives, you'll find fascinating, passionate and intelligent debates on the merits of different interfaces going right back to Xerox-PARC. They are really separate computing cultures. There's a fair historical summary here.
The above history ends in 2001. GUIs did not end there, the debate has moved further, and many new things have not been well analysed. Mobile, which essentially emulates button-based handheld appliances, cannot really be compared to GUI (in its traditional sense), even though it's technically a computer running a graphical interface.
It's only since about 2010 that the GUI function of abstracting (hiding away complexity) was subverted by wicked corporations to hide away deception and to effect control. This shift from the abstract to the abstruse and obstructive is what we sometimes call "Dark Computing Patterns", but really it goes deeper than that - visual computing is it's own realm of psychology, politics, semiotics, iconography and subterfuge that in many cases thoroughly bastardises the function of computers qua "tools".
The GUI/TUI debate can be framed in many ways; preference, freedom, extensibility, cognitive overhead, portability, control (tweakability), depth of understanding (legibility), and more.
For me, tool longevity and stability are important. I still use the same applications and skills I learned in 1980. Some people, foolishly I think, imagine that to be a bad/anti-progressive stance. One of the most underrated abilities in computer programming is knowing when something is finished. As is the ability to just use something instead of worshipping it as a digital artefact (cue NFT "first editions of brand apps).
By contrast many of my colleagues must re-learn their entire productivity stack every few months at the whim of corporate developers or seemingly random events in "the market". I literally hear them anthropomorphising:
"Oh, Slack won't let me do that now"
"Oh, Google ate my email"
"Sorry, something broke, can you resend it please?"
Their "computers" are chaotic mystery machines, magic fun fairs where superstitious ritual ministrations must be performed. This sort of Scooby-Doo "clown computing" has no place in serious business, in my opinion. So, another hugely underrated quality that TUIs favour is stability.
Where did this mess come from? In the 1980s "home computers" created a culture of their own, and from there Apple and Microsoft, needed to counter a socially constructed but actually mythical "fear" of computers as nerdy and silly, but also "dangerous". Remember granny worrying that it would "blow up" if you typed the wrong thing?
Continuing a culture of sysadmins from the time-sharing Unix days, we created the "user" as a particular stereotype. To put it quite bluntly, we manufactured "users" to be idiots. Indeed, use of the word "users" instead of a more neutral term like "operators" is significant. The developer-user relationship today is a power relationship, and often an abusive one (in both directions).
In fact denigrating attitudes have their roots in the fragility of early software development. The "user" was an enemy who would always find ways to break our software and exhibit extraordinary "stupidity" by failing to understand our non-obvious interface puzzles. We used tropes like (P.E.B.K.A.C), lusers, and treated others with disrespectful and superior smugness.
Computing had its hashtag moment, and markets demanded that perceptions change. Microsoft solved the problem by erecting some soothing blue fire-hazard cladding around a crumbling DOS. Underneath, exposure to "The Registry" was like staring directly into the open core of Chernobyl.
At that point, enter Apple, who could play Good Cop, adding value by simply subtracting (or consolidating) features. For many, Steve Jobs was elevated to the man who "invented computers". For a certain generation, he did. The ancient science of HCI (human computer interaction) was beaten and disfigured into the designer denomination of UX/UI that emphasised intuition, feel, and experience, which in turn ushered in the age of performative productivity. This trajectory of form over function culminated in neurotic obsessions with $2000 disposable thin laptops and the Onion's infamous Apple Wheel parody that confused many as to whether it was a genuinely good idea.
Meanwhile the command line simply kept calm and carried on. Nothing changed in 30 years. Those who ran the servers, databases, scientific and technical applications never strayed far from the console, except where "presentation" demanded. However, through the mass media and advertising, digital technology became synonymous with these corporate veneers over actual computers, while Hollywood made the command-line a glowing green preserve of malcontents bent on destroying civilisation.
So, although the Command Line Challenge is fun - and I hope it inspires some people to go beyond their comfort zone - let's be aware that human factors, history and politics play a greater role behind the scenes. Yes, it's about mental models, rote motor skills and habits, rather than any intrinsic good or bad. But it's also about culture and popular ideas of what a computer "is".
The emphasis of Cheapskate's article is on TUI allowing the use of older computers. That's a very topical and important concern in the age of climate emergency. If readers don't know already about books like Gerry McGovern's World Wide Waste, I urge you to read more about e-waste. Making the connections between textual interfacing, more modest tech-minimalist use, and a better society and healthier planet, isn't obvious to everyone.
There are many reasons people may prefer to return to the command line. I vastly prefer TUI's for another reason. As a teacher I deal in ideas not applications, so it's a way of imparting lasting concepts instead of ephemeral glitter. Commands are connections of action concepts to words, essential for foundational digital literacy. Almost everything I can teach (train) students to use by GUI will have changed by the time they graduate.
For younger people the difference is foundational. My daughter and I sit down together and do basic shell skills. She can log in, launch an editor, play music and her favourite cartoon videos. We use Unix talk to chat. It's slow, but great fun, because character based coms is very expressive as you see the other person typing. She's already internalising the Holy Trinity - storage, processing and movement.
To make this work I obviously customised bash, creating a kind of safe sandbox for her with highly simplified syntax. This week we are learning about modifier keys - shift is for SHOUTING and control is to CANCEL (you can't get around needing to teach CTRL-C). What we are really working on is her typing skills, which are the foundation of digital literacy in my opinion. I think at the age of 5 she is already a long way ahead of her school friends who paw at tablets.
In conclusion then, the TUI/GUI saga is about much more than interchangeable and superficial ways of interacting with computers. In it's essence it is about literacy, the ability to read and write (type). Behind, and ahead of it, are matters of cultural importance relevant to education, autonomy, democracy, self-expression, and the economy. So if you're a mouser or screen smudger, why not give Cheapskate's challenge a try? █
- Roy Schestowitz's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- 21911 reads
 PDF version
PDF version
20-22 Vision for Tux Machines
Submitted by Roy Schestowitz on Sunday 2nd of January 2022 03:18:03 PM Filed under
THIS year the site will turn 18 and will cross the 170,000-node threshold (some time in late summer), eclipsing the breadth and depth of many sites out there, not just GNU/Linux-centric sites.
Our plan is to not change much (Susan's tradition of "today's howtos", for instance, will be preserved and cherished). We'll try to publish blog posts more routinely, Rianne predicts she might write about animals (not only penguins), as she wants to encourage support for conservation.
Thank you for reading Tux Machines and happy new year! █
- Roy Schestowitz's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- 26890 reads
 PDF version
PDF version
An Advanced New Year's Message/Greetings From Tux Machines
Submitted by Roy Schestowitz on Wednesday 29th of December 2021 02:37:36 PM Filed under
ABOUT two days from now, depending on your local timezone, 2021 will be over. It's almost December 30th -- 30 minutes away to be precise -- in JST.
2021 was very good to us. We served about 190,000,000 hits, we published about 18,000 nodes, and about half a dozen regular contributors were involved, both behind the scenes and in public. In 2022 we'll turn 18.
Earlier this year we moved our IRC channel from the Freenode network to the Techrights network and days ago we published all the IRC logs. They tell quite the story. █
- Roy Schestowitz's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- 22651 reads
 PDF version
PDF version
Tux Machines at 160,000 Nodes
Submitted by Roy Schestowitz on Monday 27th of December 2021 03:22:53 AM Filed under
A number of months ago, way back in June, we celebrated passing the 150,000-node milestone. In a matter of a few hours we will have posted 160,000 nodes in total, so that's about 10,000 nodes in just over 6 months. 40,000 more should take just over 2 more years assuming the publication pace remains roughly the same. In 2022 the site turns 18. █
- Roy Schestowitz's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- 25467 reads
 PDF version
PDF version
Snowfall on your Linux Desktop this Christmas
Submitted by trendoceangd on Saturday 25th of December 2021 11:27:08 AM Filed under
Let us make this Christmas special for you and more of your Linux desktop.
- trendoceangd's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 21577 reads
 PDF version
PDF version
December 25th...
Submitted by Roy Schestowitz on Saturday 25th of December 2021 03:21:21 AM Filed under

TOMORROW we shall publish IRC logs for the whole year. It's this time of the year again. News is expected to be a lot slower over the weekend, but we'll stay on top of it regardless.
- Roy Schestowitz's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- 22143 reads
 PDF version
PDF version
Proxychains – Run Commands and Applications using Proxy Tunnels
Submitted by trendoceangd on Monday 20th of December 2021 03:36:17 PM Filed under
Require to run commands and applications through secure tunnel of Tor nodes?
- trendoceangd's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 25868 reads
 PDF version
PDF version
Proxychains – Run Commands and Applications using Proxy Tunnels
Submitted by trendoceangd on Monday 20th of December 2021 03:36:16 PM Filed under
Require to run commands and applications through secure tunnel of Tor nodes?
- trendoceangd's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 14454 reads
 PDF version
PDF version
Install and Configure Mutt Command-Line Email Client
Submitted by trendoceangd on Wednesday 15th of December 2021 03:51:01 PM Filed under
Are you DevOps engineer working on cloud infrastructure connected with your remote Linux server.
- trendoceangd's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 22406 reads
 PDF version
PDF version
Creating executable file for python program
Submitted by trendoceangd on Monday 13th of December 2021 04:54:49 PM Filed under
Finally, you have finished your python program and wanted to share someone else.
- trendoceangd's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 23418 reads
 PDF version
PDF version
Migrate google chrome web browser profiles and settings from Windows to Linux?
Submitted by trendoceangd on Sunday 12th of December 2021 12:02:21 PM Filed under
Google chrome is one of the most popular application in the world of browser.
- trendoceangd's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 22743 reads
 PDF version
PDF version
Best PDF reader/viewer for Linux
Submitted by trendoceangd on Sunday 12th of December 2021 08:31:09 AM Filed under
Finding the best PDF readers suitable and fulfilling all your needs? Then you are in the right place.
- trendoceangd's blog
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 23754 reads
 PDF version
PDF version
More in Tux Machines
- Highlights
- Front Page
- Latest Headlines
- Archive
- Recent comments
- All-Time Popular Stories
- Hot Topics
- New Members
today's howtos
|
Red Hat Hires a Blind Software Engineer to Improve Accessibility on Linux Desktop
Accessibility on a Linux desktop is not one of the strongest points to highlight. However, GNOME, one of the best desktop environments, has managed to do better comparatively (I think).
In a blog post by Christian Fredrik Schaller (Director for Desktop/Graphics, Red Hat), he mentions that they are making serious efforts to improve accessibility.
Starting with Red Hat hiring Lukas Tyrychtr, who is a blind software engineer to lead the effort in improving Red Hat Enterprise Linux, and Fedora Workstation in terms of accessibility.
|
Today in Techrights
|
Android Leftovers |













.svg_.png)
 Content (where original) is available under CC-BY-SA, copyrighted by original author/s.
Content (where original) is available under CC-BY-SA, copyrighted by original author/s.

Recent comments
30 weeks 3 days ago
30 weeks 3 days ago
30 weeks 4 days ago
30 weeks 4 days ago
30 weeks 4 days ago
30 weeks 4 days ago
30 weeks 4 days ago
30 weeks 5 days ago
30 weeks 5 days ago
30 weeks 5 days ago