SUSE
Good news everyone! SLE 15 SP4 is now released
Submitted by Roy Schestowitz on Friday 24th of June 2022 01:57:18 PM Filed under
![]()
The SLE engineering team is excited to announce that SLE 15 SP4 is now available for download!
We have been working hard to make this release as boring smooth as possible for our users, despite updating at least 23% of our entire code and syncing selected packages from openSUSE Factory. Countless internal person-hours was required for developing, testing, releasing, documenting this new Refresh Service Pack and yet we also have to thank our Public Beta testers, our Technology Partners and of course our openSUSE community for their priceless contribution! Releasing our SUSE Linux Enterprise product Family is a truly collective effort, so thank you all!
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 3708 reads
 PDF version
PDF version
All-in on PipeWire for openSUSE Tumbleweed
Submitted by Roy Schestowitz on Wednesday 22nd of June 2022 06:09:34 PM Filed under

I have written about using PipeWire previously where I did have a very positive experience with it. Unfortunately, I did have some irritating quarks with it that ultimately resulted in my going back to using PulseAudio on my openSUSE Tumbleweed machines. They were little things needing to refresh the browser after a Bluetooth device changed status. I decided it was time to try PipeWire again when PulseAudio started to give me random Bluetooth audio device issues where the device, after connecting, would not become available.
I have heard about many of the improvements that had come to PipeWire and decided that now was the time to try it out again. I revisited the directions I had previously put together on the installation process and sure enough it worked. I did have to make one modification to it. I added a now new module called pipewire-aptx which is the Bluetooth aptX codec plugin.
If you have an installation of openSUSE Tumbleweed that is using the PulseAudio sound server, the command is quite simple to execute in the terminal to switch you over. I have tested and verified this on multiple machines with success.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2590 reads
 PDF version
PDF version
Review: openSUSE 15.4 Leap
Submitted by Rianne Schestowitz on Monday 20th of June 2022 11:52:44 AM Filed under

openSUSE is a project which almost always impresses me with its technology, its integration, and its flexibility. However, it's never a distribution I've run as my main operating system for various reasons. One of the main reasons I haven't fully embraced openSUSE, despite its many technological capabilities, is its inconsistent polish. Some aspect of the operating system are polished and developed to near perfection. The installer is both fairly easy to navigate and surprisingly flexible. The default Btr filesystem is powerful and its snapshots easy to use. The YaST control panel is remarkably good at adjusting low level aspects of the operating system and integrates nicely with Btrfs.
However, on the other side of things, we have issues like the KDE Wallet utility nagging the user and displaying vague prompts about which cryptography functions to use. The live media offers a different and quite less appealing experience than the installed operating system, and (despite the progress in this arena) the documented steps to install media codecs are still some of the most complex in the Linux ecosystem.
openSUSE 15.4 feels like a distribution by system administrators for administrators. We can set up a printer and rollback filesystem snapshots with a few clicks of the mouse, but installing video codecs is a two-commands-and-four-prompts command line process. Managing services and setting up network shares takes just a few clicks, but getting sound working on the live disc was an exercise in frustration. openSUSE is a distribution which makes a lot of usually hard tasks easy and the normally easy tasks hard.
In short, some parts of openSUSE feel like the Iron Man nanotech suit and some parts feel like they were built in a cave. The former parts definitely outweigh the latter, but the little issues are what separate a good, solid distribution from a great experience.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 3022 reads
 PDF version
PDF version
OpenSUSE: Base Container Images (BCI) and ALP Quality Engineering
Submitted by Roy Schestowitz on Thursday 16th of June 2022 03:42:35 PM Filed under
-
BCI test tutorial - openQA bites
Base Container Images (BCI) are a SUSE offer for a variety of container images suitable for building custom applications atop of the SUSE Linux Enterprise (SLE). They are a suitable building platform for different container applications and are available for free without subscription. In this blog post I’m covering how we test BCI before they are released and how you can run individual tests on them.
-
An update from ALP Quality Engineering - openSUSE News
Building our products in an open and transparent way allows us to rethink the way how we test.
Jose Lausuch from our ALP Quality Engineering was invited to the Community Workgroup weekly meeting to speak about current plans of Quality Engineering for ALP.
Jose mentioned that the QE Workgroup would like to start testing existing ALP images with the existing MicroOS test suite. The effort is coordinated in poo#112409.
- 1 comment
 Printer-friendly version
Printer-friendly version- Read more
- 3180 reads
 PDF version
PDF version
SUSE/OpenSUSE Leftovers
Submitted by Roy Schestowitz on Wednesday 15th of June 2022 06:01:23 PM Filed under
-
Kubewarden is now part of CNCF Sandbox | SUSE Communities
This is a great achievement for the whole team and is the beginning of our journey into CNCF. Also, many thanks to the CNCF TOC for the feedback they provided during the project evaluation.
-
How to install openSUSE 15.4 - Invidious
In this video, I am going to show how to install openSUSE 15.4.
-
Community aims to grow communication, marketing team [Ed: openSUSE uses proprietary software for communications]]
The openSUSE community has been having community meetings on a regular basis for some time and attendees in the latest meeting have expressed a desire to grow the communications and marketing team.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2782 reads
 PDF version
PDF version
Events: Patrick Masson, Linux Plumbers Conference, and SUSECON
Submitted by Roy Schestowitz on Tuesday 14th of June 2022 10:28:59 PM Filed under



-
Higher Ed needs to step up to stay relevant as Open Source floods the IT world [Ed: So this is where Patrick Masson moved to after he quit OSI; Danese Cooper Cooper, who worked for famous criminal Bill Gates, is there too]
Grant money is pouring in to support institutions of higher education that are taking a strong position in the adoption of Open Source technologies. 82% of enterprise IT leaders are choosing to work with Open Source vendors, and higher education is stepping up and following suit. In order to stay competitive, campuses must take a critical look at how they manage IT portfolios and seriously consider a larger commitment to their own Open Source strategy.
-
Registration Currently Sold Out, We’re Trying to Add More Places – Linux Plumbers Conference 2022
Back in 2021 when we were planning this conference, everyone warned us that we’d still be doing social distancing and that in-person conferences were likely not to be as popular as they had been, so we lowered our headcount to fit within a socially distanced venue. Unfortunately the enthusiasm of the plumbers community didn’t follow this conventional wisdom so the available registrations sold out within days of being released. We’re now investigating how we might expand the venue capacity to accommodate some of the demand for in-person registration, so stay tuned for what we find out.
-
SUSECON 2022 highlights include container management, edge [Ed: SUSE is selling complexity instead of GNU/Linux. It's also a proprietary software reseller.]
SUSE's annual global conference, SUSECON, held virtually in June, was jam-packed with initiatives and information essential for the future of SUSE and for the open source market.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 3139 reads
 PDF version
PDF version
YaST in a YaST-less system
Submitted by Roy Schestowitz on Monday 13th of June 2022 07:29:39 PM Filed under
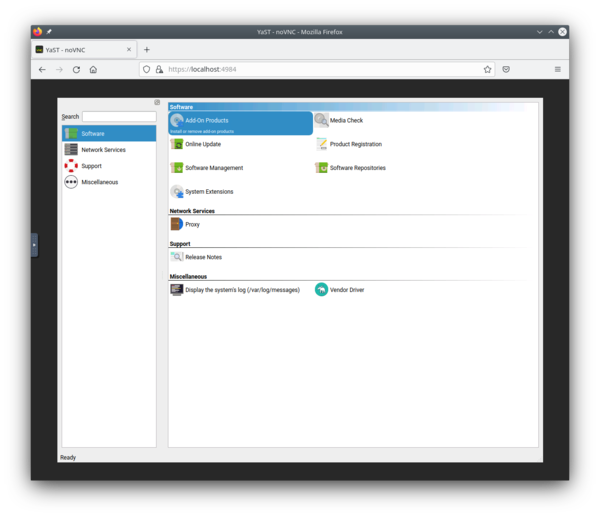
We all know how awesome YaST can be for administering your (open)SUSE system. From managing the software repositories and the installed software to adjusting the systemd services and sockets. From creating LVM logical volumes to configuring Kdump (or fadump). From inspecting the systemd journal to fine-tuning the boot loader. From configuring network interfaces to adjusting the mitigations for CPU vulnerabilities. From setting the firewall configuration to managing your subscriptions to the different SUSE products… and so much more!
But all that comes with a pretty obvious price. You must install YaST and all its dependencies in the system you want to manage. Those dependencies include the Ruby runtime, either ncurses or Qt (depending if you want the text-based or the fully graphical interface) and some other packages or libraries depending on what you want to achieve. For example, you need libzypp to install software or to manage the repositories.
What if you don’t want to pay that price? Well, we have an special offer for you! Now you can use YaST to administer your system without installing YaST or any of its dependencies. Ideal for lovers of minimal systems like the MicroOS variants of SUSE and openSUSE. All you need is a container engine like Docker or Podman… and you are using one anyways if you are using MicroOS, isn’t it?
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2726 reads
 PDF version
PDF version
Review: openSUSE Leap 15.4
Submitted by Roy Schestowitz on Friday 10th of June 2022 07:29:33 PM Filed under


The Reg FOSS desk took the latest update to openSUSE's stable distro for a spin around the block and returned pleasantly impressed.
As we reported earlier this week, SUSE said it was preparing version 15 SP4 of its SUSE Linux Enterprise distribution at the company's annual conference, and a day later, openSUSE Leap version 15.4 followed.
The relationship between SUSE and the openSUSE project is comparable to that of Red Hat and Fedora. SUSE, with its range of enterprise Linux tools, is the commercial backer, among other sponsors.
The picture is complicated by the fact that there are two different openSUSE distributions: Leap and Tumbleweed. Tumbleweed is a rolling-release distro, akin to Arch Linux; there's no stable version, and new packages emerge from the project's Factory every day.
In contrast, Leap is one of the most stable distros available. Major releases appear approximately every few years, with a new minor or point release annually. Since the last point release, 15.3, the project has synchronized its codebase with the enterprise distro. This makes it possible to migrate an installation of openSUSE Leap to the paid SLE product and receive commercial support.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2684 reads
 PDF version
PDF version
openSUSE Leap 15.4 - What's new, download details and roadmap to 15.5
Submitted by arindam1989 on Thursday 9th of June 2022 07:26:05 AM Filed under

A release roundup of the rock-solid openSUSE Leap 15.4 which brings several updates to desktops, servers, containers and virtual workloads.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2653 reads
 PDF version
PDF version
openSUSE Leap 15.4 Officially Released, This Is What's New
Submitted by Marius Nestor on Wednesday 8th of June 2022 12:08:08 PM Filed under



Derived from and fully binary identical with the recently released SUSE Linux Enterprise 15 SP4 (Service Pack 4), openSUSE Leap 15.4 comes a year after the openSUSE Leap 15.3 release and it's powered by the Linux 5.14 kernel series, which is maintained by SUSE.
This release comes with a unified feature set, as well as a seamless migration experience for those who want to move their workloads from the commercial SUSE Linux Enterprise Server to the free openSUSE Leap operating system.
- 4 comments
 Printer-friendly version
Printer-friendly version- Read more
- 3369 reads
 PDF version
PDF version
More in Tux Machines
- Highlights
- Front Page
- Latest Headlines
- Archive
- Recent comments
- All-Time Popular Stories
- Hot Topics
- New Members
digiKam 7.7.0 is released
After three months of active maintenance and another bug triage, the digiKam team is proud to present version 7.7.0 of its open source digital photo manager. See below the list of most important features coming with this release.
|
Dilution and Misuse of the "Linux" Brand
|
Samsung, Red Hat to Work on Linux Drivers for Future Tech
The metaverse is expected to uproot system design as we know it, and Samsung is one of many hardware vendors re-imagining data center infrastructure in preparation for a parallel 3D world.
Samsung is working on new memory technologies that provide faster bandwidth inside hardware for data to travel between CPUs, storage and other computing resources. The company also announced it was partnering with Red Hat to ensure these technologies have Linux compatibility.
|
today's howtos
|






.svg_.png)
 Content (where original) is available under CC-BY-SA, copyrighted by original author/s.
Content (where original) is available under CC-BY-SA, copyrighted by original author/s.

Recent comments
47 weeks 1 day ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 3 days ago
47 weeks 3 days ago
47 weeks 3 days ago