Sci/Tech
“Why I Hate Elon Musk”
Submitted by Roy Schestowitz on Tuesday 26th of April 2022 12:08:31 AM Filed under


Video download link | md5sum 526954e8bf862702e446d6cce5e152b0
Why I Hate Elon Musk | Credit to original author here
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 11026 reads
 PDF version
PDF version
Linux on Mars: 17 flights later
Submitted by Roy Schestowitz on Wednesday 23rd of March 2022 12:15:48 PM Filed under



Last year was a big year for Linux, as the operating system (OS) played a critical role in a major achievement: the first-ever powered flight on another planet. On 19 April last year, the Ingenuity drone – or “Mars Helicopter”, as NASA calls it – took to the skies of Mars. Under the hood, the on-board computer was running Linux.
Last year, we spoke with Tim Canham, the software and operations lead on the project, who shared with us details of how the helicopter works. Now, a staggering 17 successful flights later, we thought it was time to check in on the helicopter’s progress.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2548 reads
 PDF version
PDF version
Gnuastro 0.17 released
Submitted by Roy Schestowitz on Sunday 20th of March 2022 09:49:30 PM Filed under

Dear all, I am happy to announce the 17th official release of GNU Astronomy Utilities (Gnuastro). As you see in [1] below, many useful new features have been added, and many bugs have been found and fixed. Thanks to 8 people who directly committed into Gnuastro's source (4 women and 4 men), and 20 people providing ideas that have been impleted (see below for the names). This is a new record in Gnuastro! Thanks for helping make Gnuastro better with your great contributions and feedback :-). Here is the compressed source and the GPG detached signature for this release. To uncompress Lzip tarballs, see [2]. To check the validity of the tarballs using the GPG detached signature (*.sig) see [3]: https://ftp.gnu.org/gnu/gnuastro/gnuastro-0.17.tar.lz (3.8MB) https://ftp.gnu.org/gnu/gnuastro/gnuastro-0.17.tar.lz.sig (833B) https://ftp.gnu.org/gnu/gnuastro/gnuastro-0.17.tar.gz (6.0MB) https://ftp.gnu.org/gnu/gnuastro/gnuastro-0.17.tar.gz.sig (833B) Here are the SHA1 and SHA256 checksums (other ways to check if the tarball you download is what we distributed). Just note that the SHA256 checksum is base64 encoded, instead of the hexadecimal encoding that most checksum tools default to. a14313670e0bb7f3127ffba00a935aadc441bbc5 gnuastro-0.17.tar.lz 8M02HvN6iflxKk/2MfW5dT2EADwE2tr7NaXQpLs6A78 gnuastro-0.17.tar.lz 666986a1e39b513f330fffec480e083c1d37d3e2 gnuastro-0.17.tar.gz xBvtM8wkDOqXg/Q2dNfPR0R0ZgRm4QiPJZoLDKivaPU gnuastro-0.17.tar.gz I am very grateful to (in alphabetical order) Pedram Ashofteh Ardakani, Sepideh Eskandarlou, Zahra Hosseini Shahisavandi, Raul Infante-Sainz, Sachin Kumar Singh, Elham Saremi and Nafise Sedighi for their direct contribution to the source of Gnuastro. Also, Sergio Chueca Urzay, Tamara Civera Lorenzo, Andres Del Pino Molina, Alexey Dokuchaev, Alessandro Ederoclite, Sepideh Eskandarlou, Juan Antonio Fernández Ontiveros, Zohreh Ghaffari, Giulia Golini, Martin Guerrero Roncel, Zahra Hosseini, Raúl Infante-Sainz, Alejandro Lumbreras Calle, Sebastian Luna-Valero, Samane Raji, Ignacio Ruiz Cejudo, Manuel Sánchez-Benavente, Peter Teuben, Jesús Varela and Aaron Watkins provided many good suggestions and helped in finding many bugs in the code, tutorials and documentation. If any of Gnuastro's programs or libraries are useful in your work, please cite _and_ acknowledge them. For citation and acknowledgment guidelines, run the relevant programs with a `--cite' option (it can be different for different programs, so run it for all the programs you use). Citations _and_ acknowledgments are vital for the continued work on Gnuastro, so please don't forget to support us by doing so. This tarball was bootstrapped (created) with the tools below. Note that you don't need these to build Gnuastro from the tarball, these are the tools that were used to make the tarball itself. They are only mentioned here to be able to reproduce/recreate this tarball later. Texinfo 6.8 Autoconf 2.71 Automake 1.16.4 Help2man 1.49.1 ImageMagick 7.1.0-27 Gnulib v0.1-5187-g2ca890b564 Autoconf archives v2022.02.11-1-g203f15b The dependencies to build Gnuastro from this tarball on your system are described here: https://www.gnu.org/s/gnuastro/manual/html_node/Dependencies.html Best wishes, Mohammad
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2317 reads
 PDF version
PDF version
Pi Day: Pi calculated to more than 62.8 trillion digits
Submitted by Roy Schestowitz on Monday 14th of March 2022 08:31:17 PM Filed under



Guinness World Records said Thomas Keller and his team at the Center for Data Analytics, Visualization and Simulation, or DAViS, used the software y-cruncher on a machine using the Ubuntu 20.04 operating system to create their precise calculations.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 3742 reads
 PDF version
PDF version
Could Unix Happen Today? Brian Kernighan Looks Back ... and Forward
Submitted by Roy Schestowitz on Sunday 13th of February 2022 02:35:04 AM Filed under



As beloved Unix pioneer Brian Kernighan approaches his 80th birthday, he made a special appearance at this year’s Linux Conference Australia. At the traditional January event — held virtually for the second year in a row — Kernighan reminisced on the 1970s and “The early days of Unix at Bell Labs,” always careful to acknowledge the contributions of others, and of those developers who’d preceded him.
Kernighan also used the occasion to reflect on the lessons to be learned from the history of the Unix operating system, from the C programming language, and even from Microsoft’s foray into Unix — ultimately asking the poignant question of whether a Unix-like phenomenon could ever happen again.
And finally, Kernighan also looked to the future, and expressed a sincere hope that the talk might “perhaps teach us something about how software development can be done effectively, and perhaps how to manage people and processes to make them as productive as possible.”
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 5768 reads
 PDF version
PDF version
Canonical, NASA, and Award-Winning Artist Team Up for Space Art Project
Submitted by Rianne Schestowitz on Tuesday 1st of February 2022 04:59:02 PM Filed under


Ubuntu (and Linux in general) is already used in a variety of practical space applications, from powering smart robots to helping rovers rove. But one area it’s yet to boldly go —sorry, couldn’t resist— is into the realm of cosmic creativity.
Until now, that is.
Boundary-pushing artist Cecilie Waagner Falkenstrøm and the team at ARTificial Mind want to “advance the next epoch of digital art”. Their artistic tools of choice? Ubuntu Core, artificial intelligence, and, the universe.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 3484 reads
 PDF version
PDF version
Review: CircuitMess Ringo: The Educational DIY Mobile Phone Hobby Kit
Submitted by pkoutoupis on Wednesday 19th of January 2022 03:25:17 PM Filed under




The Ringo is a fun and exciting educational kit, a do-it-yourself build your own mobile phone set that actually functions with micro SIM cards.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 3555 reads
 PDF version
PDF version
SciDAVis is an open-source application for scientific data analysis and data visualization
Submitted by Roy Schestowitz on Thursday 13th of January 2022 09:40:33 PM Filed under

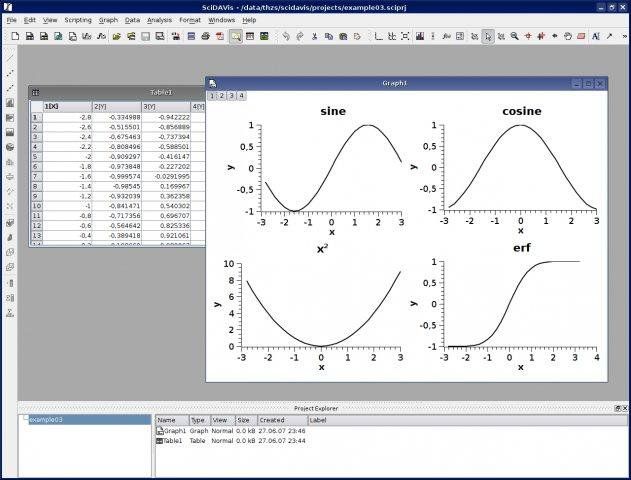
SciDAVis is a free interactive application aimed at data analysis and publication-quality plotting. It combines a shallow learning curve and an intuitive, easy-to-use graphical user interface with powerful features such as scriptability and extensibility.
Alternative to:
SciDAVis is similar in its field of application to proprietary Windows applications like Origin and SigmaPlot as well as free applications like QtiPlot, Labplot, and Gnuplot.
What sets SciDAVis apart from the above is its emphasis on providing a friendly and open environment (in the software as well as the project) for new and experienced users alike.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 3255 reads
 PDF version
PDF version
Plots is an open-source, free app to visualize visualize mathematical formulas
Submitted by Roy Schestowitz on Thursday 13th of January 2022 10:22:43 AM Filed under

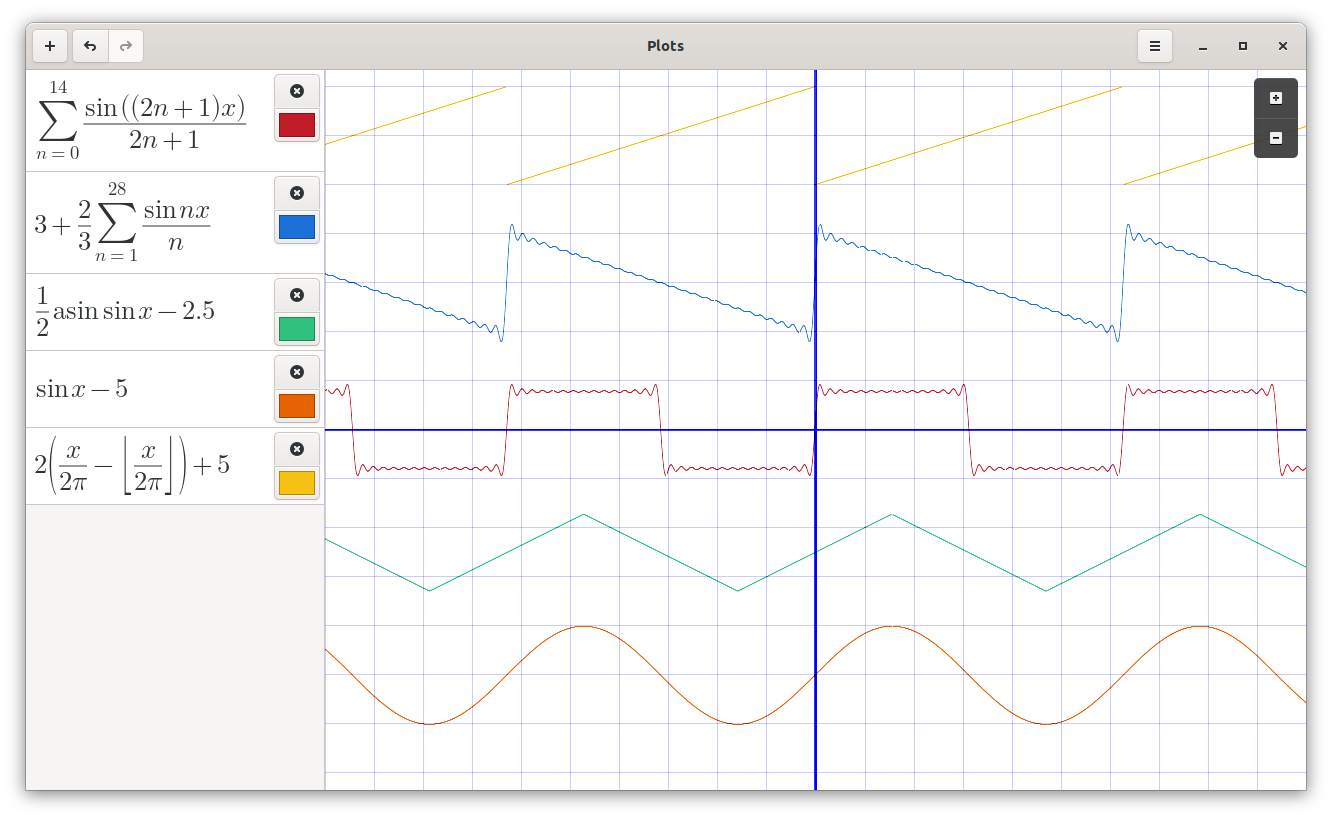
Plots is a graph plotting app for GNOME. Plots makes it easy to visualize mathematical formulae. In addition to basic arithmetic operations, it supports trigonometric, hyperbolic, exponential and logarithmic functions, as well as arbitrary sums and products. It can display polar equations, and both implicit and explicit Cartesian equations.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2933 reads
 PDF version
PDF version
Fun with Telescopes
Submitted by Roy Schestowitz on Wednesday 29th of December 2021 01:25:28 PM Filed under

Recently I purchased a small telescope to look at solar spots. When choosing a mount, I checked whether it can be controlled with OSS.
In this context INDI is mentioned everywhere and my desired mount was supported. indi and kstars are already part of Debian, so “apt install”, selecting my mount, …. oh, wait, the menu shows it, but I can not select it.
Ok, that was the time when I learned about the difference of indi and indi-3rdparty. The indi package just contains a few drivers and others are available from a different repository. This split has been done either due to different release cycles of the driver, a different OSS license of it, or just due to binary blobs without source being part of some drivers.
Fine, there are already packages of the 3rdparty-repository available from an Ubuntu PPA, so it should be no problem to add them do Debian as well.
- Login or register to post comments
 Printer-friendly version
Printer-friendly version- Read more
- 2989 reads
 PDF version
PDF version
More in Tux Machines
- Highlights
- Front Page
- Latest Headlines
- Archive
- Recent comments
- All-Time Popular Stories
- Hot Topics
- New Members
digiKam 7.7.0 is released
After three months of active maintenance and another bug triage, the digiKam team is proud to present version 7.7.0 of its open source digital photo manager. See below the list of most important features coming with this release.
|
Dilution and Misuse of the "Linux" Brand
|
Samsung, Red Hat to Work on Linux Drivers for Future Tech
The metaverse is expected to uproot system design as we know it, and Samsung is one of many hardware vendors re-imagining data center infrastructure in preparation for a parallel 3D world.
Samsung is working on new memory technologies that provide faster bandwidth inside hardware for data to travel between CPUs, storage and other computing resources. The company also announced it was partnering with Red Hat to ensure these technologies have Linux compatibility.
|
today's howtos
|







.svg_.png)
 Content (where original) is available under CC-BY-SA, copyrighted by original author/s.
Content (where original) is available under CC-BY-SA, copyrighted by original author/s.

Recent comments
47 weeks 1 day ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 2 days ago
47 weeks 3 days ago
47 weeks 3 days ago
47 weeks 3 days ago